🔐 Trezor Wallet Login: Your Complete Guide to Secure Crypto Access 🚀
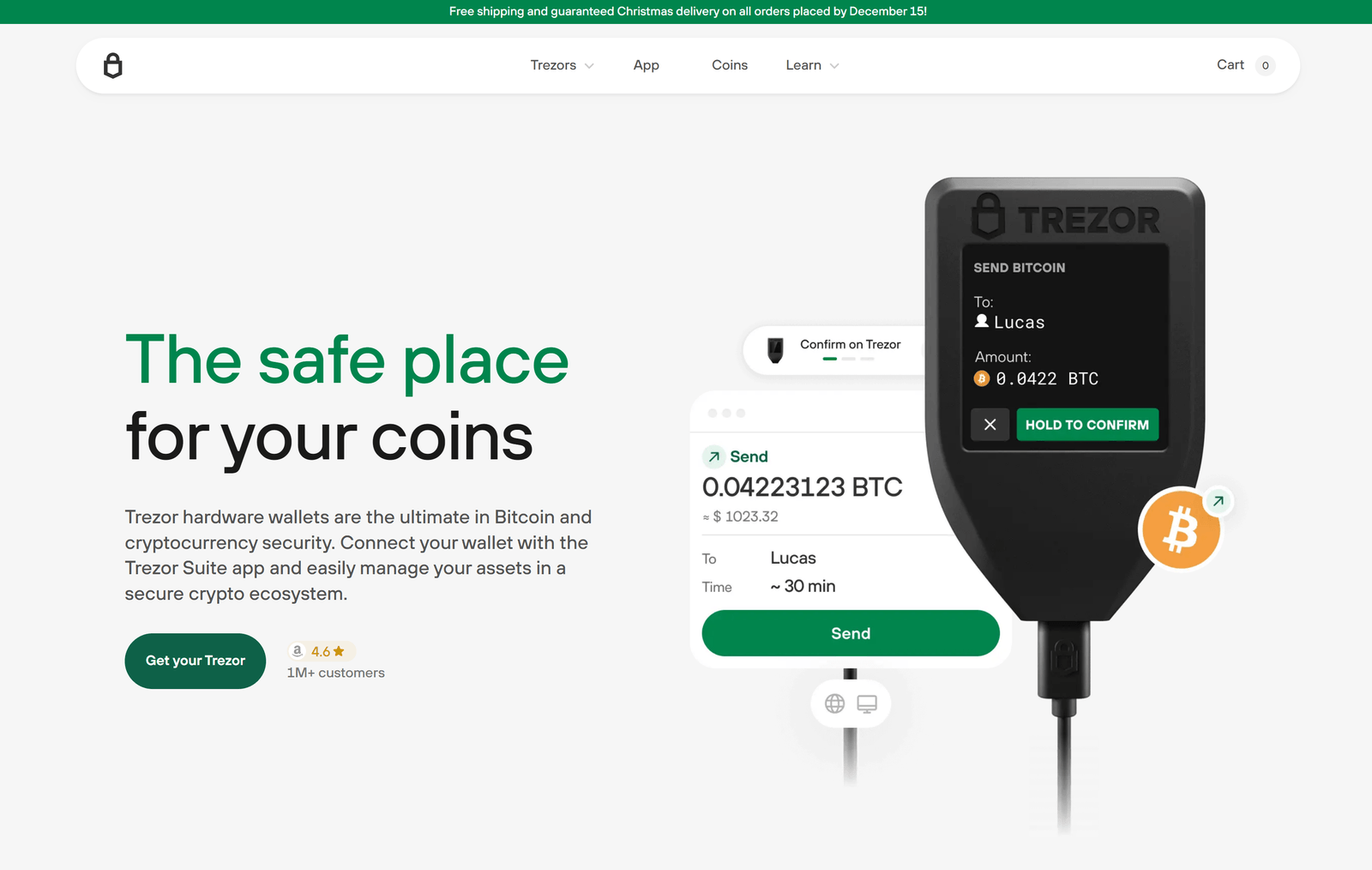
In today’s digital age, managing cryptocurrencies safely is crucial. Whether you’re a beginner or a seasoned investor, using a hardware wallet like Trezor ensures your crypto assets remain secure. One of the most critical steps in managing your Trezor wallet is the Trezor Wallet Login. This guide will walk you through the login process, security tips, and everything you need to know for a seamless experience. 💼💎
🖥️ What is Trezor Wallet?
Before diving into the login process, let’s briefly understand what Trezor is. Trezor Wallet is a hardware cryptocurrency wallet that provides top-notch security for your digital assets. Unlike software wallets, Trezor stores your private keys offline, reducing the risk of hacks and cyberattacks. 🛡️
Trezor supports multiple cryptocurrencies including Bitcoin (BTC), Ethereum (ETH), Litecoin (LTC), and many more. With its user-friendly interface and strong security measures, Trezor is the preferred choice for investors looking for safety and convenience. 🌐💰
🔑 Why Secure Login Matters
Your Trezor Wallet Login is not just a simple step to access your funds—it’s a vital security checkpoint. Every login requires confirmation via your hardware device and the Trezor Suite App. This two-step verification ensures that even if someone accesses your computer, they cannot steal your funds without the physical device. ✅🔒
Security tips for your login:
- Always connect your Trezor device directly to your computer. Avoid public USB hubs. 💻
- Never share your recovery seed. It’s the key to restoring your wallet. 🌱
- Keep your Trezor firmware updated to the latest version. 🔄
🛠️ How to Login to Trezor Wallet
Logging into your Trezor Wallet is simple, but it’s essential to follow the steps correctly:
Step 1: Connect Your Trezor Device
Plug your Trezor device into your computer using the original USB cable. Ensure the connection is secure. 🔌
Step 2: Open Trezor Suite
Download and install the Trezor Suite App if you haven’t already. Open the app to begin the login process. The Trezor Suite App is available for Windows, macOS, and Linux. 🖥️📱
Step 3: Enter Your PIN
When prompted, enter your Trezor PIN. The Trezor device will display a randomized number grid, and you’ll input the corresponding numbers on your computer. This method prevents keyloggers from capturing your PIN. 🕵️♂️
Step 4: Access Your Wallet
Once your PIN is verified, the Trezor Suite App will decrypt your wallet, giving you full access to your funds. You can now view balances, send or receive cryptocurrencies, and manage your assets securely. 💹💳
🔄 Logging in via Recovery Seed
If you ever lose your device, you can log in using your recovery seed. This is a set of 12, 18, or 24 words provided during your initial setup. Enter the seed into a new Trezor device to restore access to your wallet. ⚡🌱
Important: Keep your recovery seed offline. Never store it on your phone, computer, or cloud storage. Treat it like gold—it’s the master key to your crypto. 🏆
📱 Mobile Access with Trezor Wallet
Trezor also supports mobile devices through third-party apps that integrate with the wallet. While login on mobile is convenient, it’s essential to ensure your mobile device is secure. Always verify apps from official sources and avoid public Wi-Fi when accessing your wallet. 📶📲
🛡️ Advanced Security Features
Trezor goes beyond the standard login process to protect your assets:
- Passphrase Protection: Add an extra word to your seed phrase for enhanced security. 🔑
- Two-Factor Authentication (2FA): Use Trezor for secure 2FA on supported platforms. 📲
- Firmware Updates: Regular updates patch vulnerabilities and enhance features. ⚙️
By combining these features with your secure login, your cryptocurrency remains virtually impenetrable. 🔒✨
💡 Tips for a Smooth Trezor Login
- Always double-check the website or app URL before logging in to avoid phishing scams. 🕵️♀️
- Keep your Trezor device firmware up to date. 🔄
- Use a strong and unique PIN for added security. 🧩
- Backup your recovery seed safely. Consider using a fireproof and waterproof storage. 🔥
🌟 Conclusion
The Trezor Wallet Login is more than just entering a PIN—it’s your first line of defense against digital theft. By following the steps above and maintaining best security practices, you can enjoy seamless access to your cryptocurrencies while keeping them safe. Whether you are sending, receiving, or managing crypto assets, Trezor ensures your funds remain secure. 🏦💫
Remember, your crypto security begins with a strong login. Treat your device and recovery seed with care, update firmware regularly, and stay vigilant against phishing attempts. Your digital wealth deserves nothing less than Trezor-level protection. 🚀🔐
Start your secure journey with Trezor today and experience peace of mind in the crypto world! 🌍💎